Metasploit Community 4.1.2 Crack Free For PC [Latest]
- conseralmons
- Jun 5, 2022
- 6 min read
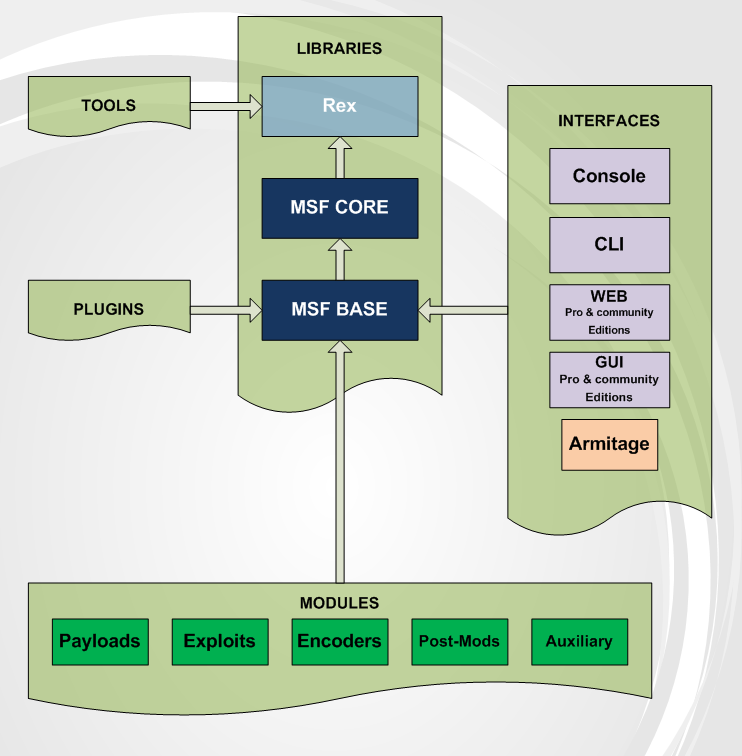
Metasploit Community 4.1.2 Full Product Key Free Download [Mac/Win] Metasploit is a powerful penetration testing and vulnerability assessment (Vulnerability Assessment) tool, with a multitude of features and capabilities. Metasploit is an integral part of the IDS/IPS field, and is often used as a pen-testing or ethical hacking framework. Metasploit is also used by security professionals for auditing or penetration testing. With Metasploit, you will be able to capture sessions, collect evidence, develop exploits and understand the application structure in order to analyze vulnerabilities. Metasploit Features: · Audit vulnerable hosts in real-time · Generate exploits for known vulnerabilities · Develop your own custom exploits · Easily generate penetration testing scripts · Use Python, Ruby, or Perl for easy scripting · Use IPython and Jupyter for data analysis · View both the attacker and defender’s perspective during a penetration test · Assess the security of applications · Test network services (e.g. SMTP, NTP) · View discovery information about the host · View all the metadata for any session · Find vulnerabilities · Test for signatures, valid credentials, known exploits, etc. · Examine all aspects of the application, from an administrator’s perspective · Explore how to use Metasploit as a framework for other penetration testing or ethical hacking tools. Overview of Metasploit: Metasploit is often called the “Swiss Army knife of pen testing”. The tool is extremely powerful and widely used for penetration testing and ethical hacking. Metasploit offers the following functionalities: · Develop custom exploits · Generate and execute exploits · Capture a system’s screen · Find out information about vulnerabilities · Analyze scripts and generate custom exploits · Evade a proxy server or any other kind of network filtering · Annotate, tag, and tokenize vulnerabilities in custom exploits · Create and view module profiles · Log and capture sessions for later review · Locate exploits and vulnerabilities from raw data · Perform reverse engineering · Reverse SSH brute force attacks · Identify active hosts, attack methods, and tools · View system info and test tools · Create your own RFI/RCE exploits · Test for known vulnerabilities · Test for malicious code on a system · Test for clear-text passwords · Perform a DNS discovery scan · Identify and enumerate active processes, Metasploit Community 4.1.2 Free Download X64 Metasploit Community is a professional software application specialized in offering information about security vulnerabilities with the aid of penetration testing tools. It provides support for network discovery, vulnerability scanner import, basic exploitation and module browser. Web-based interface and user setup The program runs as a web server on your computer and can be accessed via your web browser. In order to access the service, you are required to provide information about the username, password, full name, email address and organization, as well as select the time zone. All your penetration tests are recorded as projects, and the tool comes with a set of predefined ones useful for getting started with, such as Hosts, Notes, Vulnerabilities, Services, Captured Data, Tasks, Sessions and Campaigns. The utility also displays a project overview, which includes details about the discovered hosts, opened and closed sessions and collected evidence. Create a new project You may define your own project by specifying the name, adding a short description and entering the network range. Within a project, you are given the freedom to define target systems, network boundaries, modules and web campaigns, as well as use discovery scan mode for identifying target systems and bruteforce attack for gaining access to systems. Administrator features Administrators are given the possibility to carry out several tasks, such as manage projects, accounts, global settings and software updates. When it comes to global settings, you can set the payload type for the modules, enable access to the diagnostic console through web browser, as well as update the license key and perform software updates. Host scan mode Metasploit Community comes with a powerful host scan feature able to identify vulnerable systems within the target network range. It records information about the services, vulnerabilities and captured evidence for hosts. Plus, you can add vulnerabilities, notes, tag and tokens to identified hosts. An exploit can be executed from the Modules menu by using the search engine for finding a specific engine and defining the target hosts, payload options, module and advanced parameters, as well as evasion options. The purpose of an exploit is to target a specific vulnerability detected in your system, including buffer overflow, code injection and web application exploits. Bottom line The Community edition is suitable especially for students or small businesses as it includes a limited set of features. If you are an IT security professional, you can check out the professional version of the application, which integrates support for smart exploitation, advanced vulnerability verification, password audition, web application scanning mode, social 80eaf3aba8 Metasploit Community 4.1.2 Crack + Easy to use and very effective... ...an official module to utilize the Cisco IOS update process for security patches and enhancements. Vulnerability Management for Cisco IOS is a web-based application designed to assist in the implementation and management of Cisco IOS security patches and enhancements. It is an off-line application that can be run independently of the operating system and can be accessed via web browser. The application allows for the entry of a Cisco IOS Software version and includes the required Cisco IOS Software version update or enhancement release as well as the corresponding security patches and enhancements. In addition, it allows for the selection of a specific Cisco IOS Software release as well as the selection of a specific vulnerability and the associated fixes. The application utilizes the OpenVAS platform as its vulnerability assessment engine. Use Cases A tool that allows vulnerability assessment to be performed on Cisco IOS network devices. Manages the release of Cisco IOS patches and enhancements and provides a secure way to manage this activity. Case Study McAfee's Test Center for Internet Security (TCS) is an application that allows for the validation of the application of Cisco IOS patches and enhancements. References (1) ...used to: * Build your own multimedia content, * Publish it online, * Make money. CDI Pro is a powerful, feature-rich multimedia production suite for professional and production-ready production, distribution, and creative professionals. Whether you're looking to create an audiobook, create an interactive eBook, upload an image gallery, or create an online video site, CDI Pro will help you make the best of your media! Create your own multimedia content CDI Pro makes creating your own multimedia content a simple task. Features such as the toolbox-based navigation, multiple templates, a flexible input and output system, easy-to-use tools, and advanced features like the powerful Audio and Video Synthesizers, provide all the tools necessary to make you the most powerful multimedia creator in the industry. Publish your work online CDI Pro provides an easy-to-use interface for publishing your multimedia content online. Have the flexibility to publish your work on any site, social network, or media outlet with CDI Pro's in- What's New In Metasploit Community? Metasploit is a popular and widely used software application for attacking systems. Metasploit is a penetration testing tool for automating the process of discovering, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit is an open source penetration testing tool developed for researchers, system administrators and computer security professionals. Metasploit is built from source code, making it the first and only penetration testing tool that is truly distributed. Metasploit is the only penetration testing tool built from the ground up as a commercial-grade, enterprise-class, software development kit that is compatible with all major operating systems and programming languages. The Metasploit Framework is a free, open source penetration testing tool for automating the process of discovering, exploiting and recovering from security vulnerabilities in enterprise networks. It is an advanced security vulnerability scanner for network discovery and enumeration. The goal of the Metasploit Framework is to automate the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. For penetration testing, Metasploit has three components: a framework, payloads and a community of developers. Metasploit’s Framework and payloads are designed for automating penetration testing. Metasploit’s Framework is a free, open source penetration testing tool for automating the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit’s Framework is the foundation for Metasploit’s second component – payloads. Metasploit’s Framework and payloads are designed for automating penetration testing. Metasploit’s Framework is a free, open source penetration testing tool for automating the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit’s Framework is the foundation for Metasploit’s second component – payloads. Metasploit’s Framework is a free, open source penetration testing tool for automating the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit’s Framework is the foundation for Metasploit’s second component – payloads. Metasploit’s Framework is a free, open source penetration testing tool for automating the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit’s Framework is the foundation for Metasploit’s second component – payloads. Metasploit’s Framework is a free, open source penetration testing tool for automating the process of discovering, enumerating, analyzing, exploiting and recovering from security vulnerabilities in enterprise networks. Metasploit’s Framework is the foundation for Metasploit’s second component – payloads System Requirements: Minimum specs: OS: Windows 7, 8.1, 10 (64-bit) Processor: Intel Core 2 Duo 2.4Ghz or faster (or AMD equivalent) Memory: 3GB RAM (4GB recommended) Graphics: ATI or Nvidia Geforce 7 series, or Intel HD 4000 or higher Hard Drive: 20GB available space DVD-ROM/CD-ROM: DVD-ROM drive with a minimum of a 4x speed and a maximum of 16x speed (DVD-R) or CD
Related links:
Comments